It’s Not If Your Email Provider Gets Hacked — It’s When
Email breaches are inevitable. What matters isn’t whether your provider gets hacked — it’s how much damage is done when it happens.

Email is one of the oldest and most trusted tools on the internet. It’s how we stay in touch with family and friends, share important moments, and reconnect — as well as how we reset passwords, receive legal notices, manage finances, and prove who we are when something goes wrong.
It’s also one of the most targeted systems in existence. Security reports from organisations like Verizon and the UK’s National Cyber Security Centre consistently show that email is the primary entry point for modern cyberattacks.
And that leads to an uncomfortable but increasingly unavoidable truth:
It’s not if your email provider gets hacked — it’s when.
That statement isn’t alarmist. It’s realistic.
Modern security doesn’t assume perfection
In cybersecurity, there’s a principle known as assume breach.
It means systems aren’t designed around the idea that nothing will ever go wrong. They’re designed around the expectation that something eventually will — and that when it does, the damage should be limited, contained, and recoverable.
This mindset already exists in other areas of life:
- We wear seatbelts without expecting a crash
- We lock doors without expecting a burglary
- We back up data without expecting failure
Email security deserves the same realism.
On this page
- Modern security doesn’t assume perfection
- Why email is such a valuable target
- Breaches are normal at scale
- A short timeline of real-world email breaches
- 2013–2014: Yahoo — the largest email breach on record
- 2017: Yahoo Mail forged cookie attack
- 2021: Microsoft Exchange Server attacks
- 2022–2024: Account takeovers, not headline breaches
- The pattern is consistent
- The most common ways email accounts are compromised
- The difference isn’t prevention — it’s impact
- The house alarm problem
- Privacy isn’t about hiding — it’s about access
- The real cost of getting this wrong
- This isn’t about fear — it’s about proportionality
- What comes next
- FAQ
- Final thought
Why email is such a valuable target
Email isn’t valuable only because of what you write in it.
It’s valuable because it sits at the centre of both your personal life and your digital identity.
An inbox can hold private conversations with family and friends, personal subscriptions, travel details, receipts, medical messages, and years of quiet context about who you are and how you live. Even when messages feel mundane, they build a detailed picture over time.
At the same time, email acts as the control layer for almost everything else you use online. It:
- Resets your passwords
- Verifies your identity
- Receives one-time codes
- Authorises new devices
- Connects every other account you own
For attackers, compromising an inbox often means gaining access to both personal information and the keys to everything downstream.
That’s why email providers — whether free or paid — are under constant attack.

Breaches are normal at scale
Every major platform has experienced security incidents. Some are public, some are quietly resolved, and some are only understood years later.
Large services like Gmail, Outlook, and Yahoo Mail operate at extraordinary scale, making them permanent, high-value targets.
But size alone isn’t the issue.
The real question is what happens after something goes wrong.
One reason breaches and account takeovers keep happening is simple scale. Free email services sit behind billions of accounts — and that makes them permanent, high-value targets.
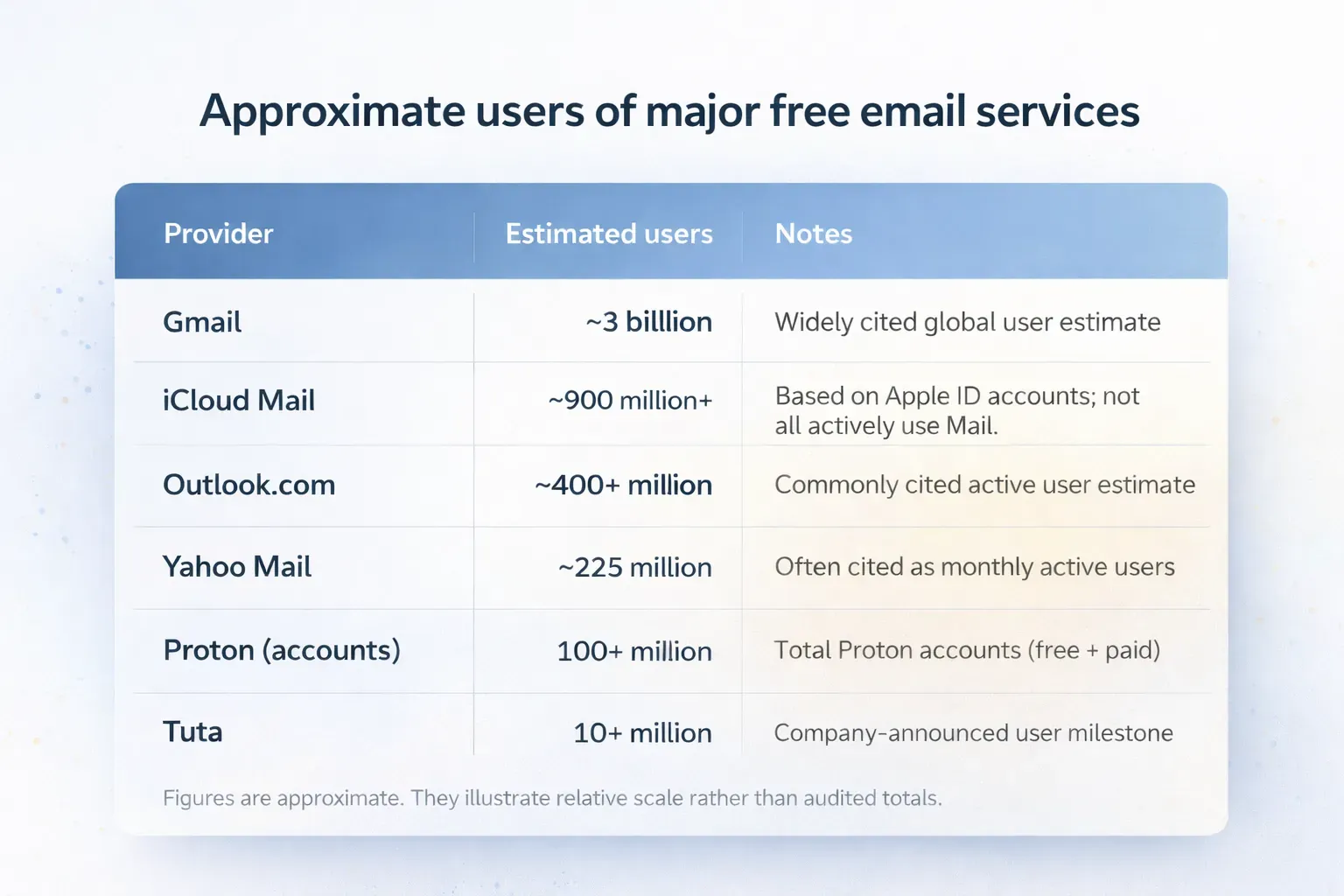
Figures are approximate and mix “accounts” and “active users” depending on what providers disclose. They’re useful for understanding relative scale, not as audited totals.
A short timeline of real-world email breaches
Email breaches aren’t hypothetical. They’re recurring, well-documented, and increasingly expected at scale.
Here are a few notable examples that show the pattern.
2013–2014: Yahoo — the largest email breach on record
Yahoo
- All 3 billion Yahoo accounts were ultimately affected
- Names, email addresses, dates of birth, and hashed passwords exposed
- Full details only emerged years after the initial breach
Reporting initially referenced 1 billion accounts, but later disclosures confirmed that all Yahoo accounts in existence at the time — around 3 billion — were affected across multiple breaches. (BBC News)
Why it matters
The scale alone made containment impossible. It also showed how long large providers can operate without fully understanding — or disclosing — the extent of a compromise.
2017: Yahoo Mail forged cookie attack
Yahoo Mail
- Attackers used forged cookies to access accounts without passwords
- Accounts were accessed silently, without user interaction
Why it matters
Not all breaches involve stolen passwords. Some bypass authentication entirely — and users may never know.
2021: Microsoft Exchange Server attacks
Microsoft
- On-premises Exchange servers exploited worldwide
- Hundreds of thousands of organisations affected
- Email access enabled follow-on attacks, ransomware, and espionage
Why it matters
Email is often the entry point, not the final target. Once attackers gain inbox access, trust and context do the rest.
2022–2024: Account takeovers, not headline breaches
In recent years, fewer incidents make headlines — but compromises are more frequent:
- Credential stuffing using old breach data
- OAuth abuse
- Malicious inbox rules and forwarding
- Silent data exfiltration
Why it matters
The threat model has shifted from dramatic “mega breaches” to continuous, low-noise compromise.
The pattern is consistent
Across different providers, years, and attack methods, the same truths repeat:
- Email providers are permanent targets
- Breaches are often detected late
- Access matters more than message content
- Recovery is painful when systems are tightly coupled
This is why modern security thinking doesn’t ask:
“How do we prevent every breach?”
It asks:
“When a breach happens, how much damage can it actually do?”
The most common ways email accounts are compromised
Not all breaches begin with dramatic zero-day exploits or nation-state attacks. Many start with far more ordinary weaknesses — the kind that exist at scale across millions of users.
The most common entry points include:
- Weak or reused passwords When the same password is used across multiple services, a breach elsewhere can quietly unlock email accounts through credential stuffing.
- No two-step authentication Without an additional verification step, a stolen password is often all an attacker needs.
- Phishing emails Carefully crafted messages designed to look legitimate remain one of the most effective attack methods — especially when they exploit urgency or familiarity.
- Social engineering Attackers don’t always hack systems; they manipulate people. Support staff, recovery processes, and trust relationships are often targeted.
- Session or token theft In some major incidents, attackers didn’t need passwords at all — they stole or forged authentication tokens, bypassing login screens entirely.
The difference isn’t prevention — it’s impact
No email provider can honestly promise that breaches will never happen.
The meaningful difference lies in:
- How much data is exposed
- Whether emails are readable
- How quickly users can recover
- Whether support is available
- How transparently incidents are handled
In other words, blast radius matters more than bravado.
One of the most effective ways to reduce that blast radius is separating your email address from the provider itself. When your address isn’t owned by the service that gets breached, recovery becomes easier and switching stops feeling catastrophic — something I explore in more detail in Why using your own domain for email makes sense.
This is where system design, incentives, and defaults become more important than marketing claims.
The house alarm problem
Most people only take home security seriously after a burglary.
By then:
- The loss has already occurred
- Privacy has already been violated
- The alarm only helps next time
Email security works the same way.
Securing your inbox after it’s compromised helps going forward — but it doesn’t undo the damage. Password resets, account lockouts, impersonation, and lost access can cascade quickly.
Good email security is preventative, not reactive.
Privacy isn’t about hiding — it’s about access
It’s one of the most common reactions to conversations about email security. But privacy isn’t about hiding wrongdoing — it’s about boundaries. We close the curtains at night not because we’re doing anything wrong, but because some things are personal. Email deserves the same respect: even a “boring” inbox contains enough access and context to cause serious disruption if it’s compromised.
The real cost of getting this wrong
When email security fails, the cost isn’t always financial — at least not immediately.
It’s paid in:
- Time spent recovering accounts
- Stress and uncertainty
- Loss of access to essential services
- Rebuilding trust everywhere else
Those costs often far outweigh the effort or expense of securing email properly in the first place.
This isn’t about fear — it’s about proportionality
Email underpins modern digital life. Treating it as disposable or “good enough” doesn’t reflect how much depends on it.
Acknowledging that breaches are inevitable isn’t pessimistic.
It’s practical.
The important question isn’t whether your provider will face an incident — it’s whether their systems were designed with that reality in mind.
For most people, improving email security isn’t a major financial decision — it’s a small, predictable monthly cost.

What comes next
This article isn’t about recommending a specific provider or pushing a particular solution.
It’s about setting the right mental model.
I’ll explore how free and paid email providers approach this differently in a follow-up, including how business models influence security decisions, recovery options, and user trust.
Because once you accept that breaches are a matter of when, not if, the way you evaluate email services starts to change.
Final thought
Email isn’t just another app.
It’s the control panel for your digital life.
Designing — and choosing — email systems that assume failure, limit damage, and respect users isn’t paranoia.
It’s the bare minimum for the internet we now live on.
Get the weekly email
A short weekly roundup on email, privacy, and digital trust. No promos. Unsubscribe anytime.