Your Passwords Are the Weakest Link — Here’s the Fix
Most people reuse passwords without realising the risk. One breach can unlock dozens of accounts. Here’s how password managers, email aliases, and backup codes close that gap.

Every time a company announces a data breach, the same advice appears:
“Change your password.”
Most people do — for that one site.
Then they carry on using the same password everywhere else.
That’s the real problem.
The biggest risk after a breach isn’t just that one account is exposed. It’s that the same password might unlock dozens of other accounts too. That’s how small leaks turn into full digital identity takeovers.
A password manager is the tool that stops that chain reaction.
This isn’t about convenience or tech enthusiasm. It’s about limiting the damage when breaches happen — because they will.
What a Password Manager actually does
A password manager has one simple job:
make sure you never have to reuse a password again.
It does that by:
- Creating long, random passwords for each site
- Storing them securely
- Filling them in for you when you log in
- Leaving you with just one strong master password to remember
You don’t need to memorise dozens of logins. The manager handles that. Your job becomes protecting the one key that unlocks the vault.
It’s not just a storage tool. It’s a system that quietly removes one of the most common causes of account takeovers.
Why password reuse is so dangerous
When a website is breached, attackers often get a list of email addresses and passwords. Sometimes those passwords are hashed (hashed passwords are scrambled using one-way cryptographic functions), and sometimes they’re exposed in plain text. Either way, attackers don’t stop at that one site.
They take those email and password combinations and try them everywhere else:
- Email providers
- Shopping accounts
- Social media
- Cloud storage
- Financial services
If you reuse passwords, one breach can unlock many doors.
Most account takeovers don’t happen because someone “hacks” you directly. They happen because a password leaked somewhere else still works.
A password manager breaks that pattern. Every site gets its own unique password, so a breach in one place doesn’t spill into the rest of your life.
Why your email account depends on this
Your email account is the reset button for your entire digital life.
If someone gets into your email, they can:
- Reset passwords on other services
- Take over social media
- Access cloud files
- Intercept security alerts
- Lock you out of your own accounts
Protecting your email properly starts long before anyone tries to log into it. It starts with not reusing passwords anywhere else.
If the password for a random old forum is the same as your email password, that old forum is now the weak link protecting everything.
A password manager removes that hidden connection.
Are Password Managers safe?
This is the part people worry about:
“What if the password manager gets hacked?”
It’s a fair question. But compare the risks.
Without a password manager:
- You reuse passwords
- You choose shorter, memorable ones
- Your security depends on dozens of different companies never being breached
With a password manager:
- Your passwords are long and random
- Each account stands alone
- Your security depends mainly on protecting one master password
Modern password managers use strong encryption designed so that even the company running the service can’t see your stored passwords. Your vault is locked with your master password before it ever leaves your device.
This “provider can’t read your data” model is often called zero-access encryption, which I explain in more detail here.
No system is perfect. But a well-protected vault is far safer than hundreds of weak, reused passwords scattered across the internet.
What to look for in a Password Manager
You don’t need to obsess over technical details. Focus on the basics:
- Strong encryption by default
- Works on all your devices (phone, laptop, browser)
- Can generate passwords for you
- Autofills logins safely
- Supports two-factor authentication (2FA) for your account
Well-known options range from privacy-focused tools like Proton Pass to long-established mainstream managers such as 1Password, LastPass, and others.
Some of these services have faced security incidents in the past, which has led many people to look more closely at how password managers store and protect data. The key thing to understand is that modern managers are designed so your vault is encrypted before it leaves your device — meaning your master password remains the most important line of defence.
No matter which provider you choose, the real security gains come from using a password manager consistently, turning on two-factor authentication, and avoiding password reuse entirely.
Password Managers + Email Aliases: The Real Power Combo
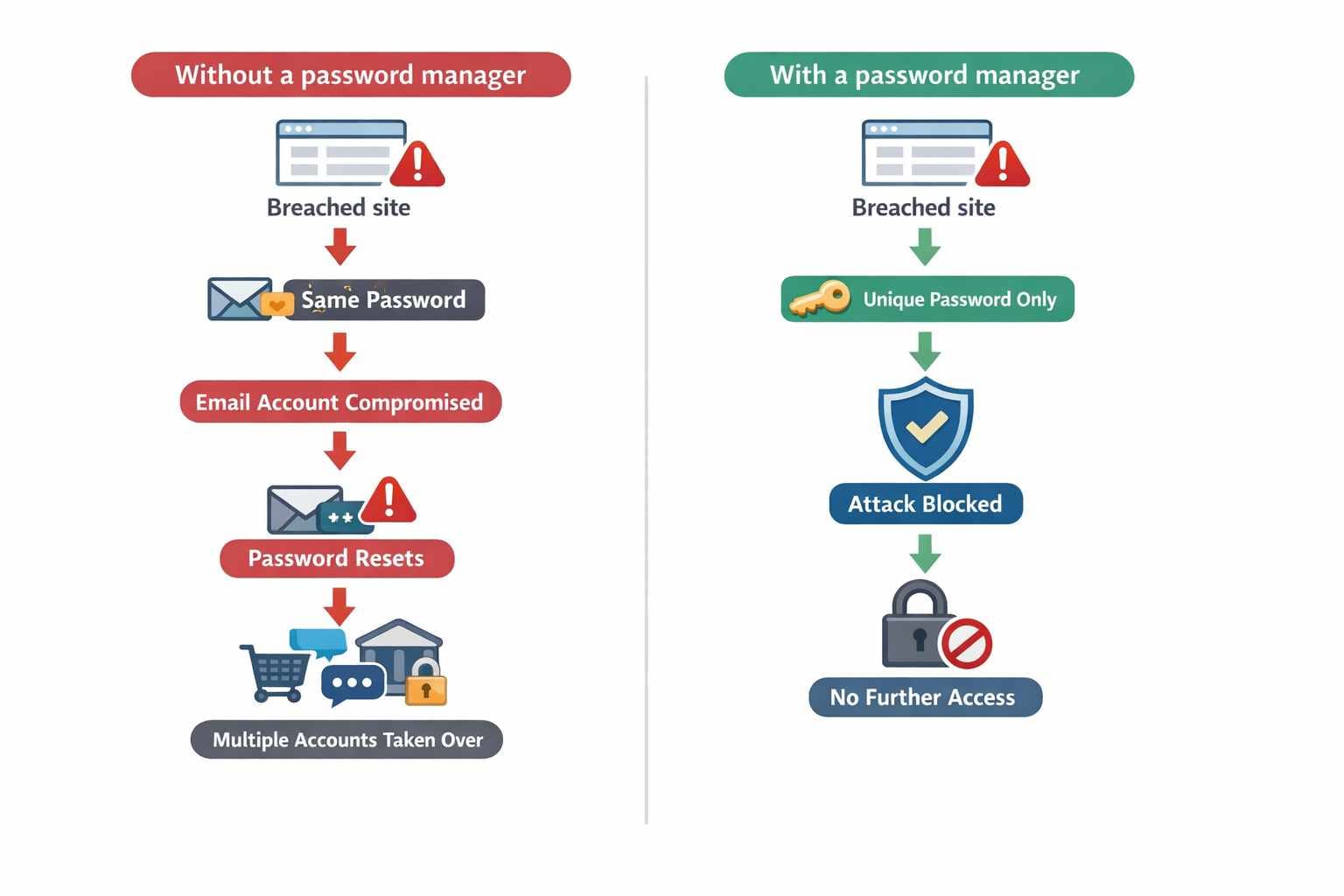
A password manager stops password reuse.
Email aliases stop identity reuse.
Used together, they change how signups work entirely.
Instead of using the same email address everywhere, you can create a unique email alias for each service. Tools like Proton Mail, StartMail, and similar privacy-focused providers let you generate multiple email addresses that all deliver to your main inbox.
Here’s why that matters:
- If one site is breached, attackers only see the alias — not your primary address
- If spam starts, you know exactly which company leaked or sold your details
- If a service is compromised repeatedly, you can disable just that alias
- Your real, long-term email address stays out of most databases
Pair that with a password manager generating a unique password for every site, and you’ve done two powerful things:
- Every account has a different password
- Every account has a different email address
Now a breach doesn’t just fail to unlock your other accounts — it also fails to point attackers at your main identity.
Signups stop being permanent identity commitments. They become connections you control.
Don’t forget the keys to your own vault
Password managers and secure email providers are designed so that only you can unlock your data.
That’s the point.
But it comes with responsibility.
Many services use encryption where even the company cannot access your vault or mailbox without your master password and recovery information. If you lose those, support can’t simply “reset” your account and give you everything back.
Imagine losing access to:
- Years of stored passwords
- Recovery codes for other accounts
- Notes and secure documents
- The list of email aliases tied to different services
That’s not just inconvenient. It can lock you out of your digital life.
Backup Codes are not optional
I’ve seen how losing account recovery access can spiral, especially when email is involved.
When you enable two-factor authentication on a password manager or email account, you’re usually given backup recovery codes.
Those codes are often the only way back in if you lose:
- Your phone
- Your authenticator app
- Your security key
- Access to your main device
Store backup codes somewhere safe and offline — printed and kept with important documents. Not in your inbox. Not in a notes app you can’t reach without logging in.
You’re not just protecting against hackers. You’re protecting against accidents.
Think about provider lock-In
Email aliases and password managers give you control — but only if you can leave when you want to.
Most reputable password managers allow you to export your vault and import it into another provider. That portability matters. It means your security isn’t trapped inside one company’s system.
Alias systems can be trickier. This is one reason I recommend thinking of email as long-term infrastructure, not just a messaging tool. Some are portable if you use your own domain. Others are provider-controlled, which means leaving can be more complicated.
That doesn’t make them bad. It just means you should understand the trade-off before building your entire login identity on them.
The Next Level: Email Aliases you actually own
Most people stop at two steps:
They use a password manager.
They start using email aliases.
That already puts them far ahead of the average internet user.
But there’s a deeper level of control that very few people think about:
Owning the identity layer itself.
The problem with provider-based aliases
Services like Proton Mail and StartMail let you create aliases under their domains. That’s a huge privacy upgrade compared to using one email address everywhere.
But those aliases still live inside someone else’s system.
If you ever leave the provider, you usually lose those addresses.
If the provider changes features, pricing, or limits, your identity structure depends on their decisions.
You’ve reduced exposure — but you haven’t fully reduced dependency.
What changes when you use your own domain
Instead of relying on provider-owned aliases, using your own domain for email means you control the addresses themselves — and can move them between services without changing your logins.
Now imagine this instead:
Your logins don’t look like
They look like
You control the domain.
You control where the mail is delivered.
You can move providers without changing your addresses.
That’s not just aliasing.
That’s portable digital identity.
Some services now make this easier by letting you generate aliases on a domain you own, then forward or host that mail wherever you choose. Tools like CatchMailNot are built around this idea: you bring the domain, they help manage the alias layer.
The result is powerful:
- Every service gets a unique address
- Breaches can be traced instantly
- You can shut down a single alias without affecting anything else
- Your identity isn’t locked to one email provider
Why this matters more over time
Email addresses are becoming long-term identity anchors.
They’re used for:
- Account recovery
- Financial services
- Government logins
- Health portals
- Two-factor authentication
If all of that is tied to an address you don’t truly control, you’re renting a key to your own digital life.
When the address is on your own domain, you’re not just organising email better.
You’re building an identity system you can carry for decades, independent of any one company.
This isn’t for everyone — yet
Using a custom domain for aliases is one step more advanced. There’s a bit of setup. You have to manage renewals. You have to think a little longer-term.
But if you already:
- Use a password manager
- Care about privacy
- Want fewer single points of failure
…then owning your alias layer is the logical next move.
It turns email from just a communication tool into something much more important:
A piece of digital infrastructure that belongs to you.
The Bigger Picture: damage control, not perfection
You can’t stop every breach. You can’t force every company to protect your data properly. And you can’t avoid creating accounts online.
What you can do is make sure a mistake in one place doesn’t spread everywhere else.
A password manager gives every account its own strong password.
Email aliases give every account its own identity.
That shift — from one address everywhere to compartmentalised identities — is how modern email privacy actually works.
Two-factor authentication adds another lock.
Backup codes make sure you don’t lock yourself out.
Portability keeps you in control long term.
None of this makes you invisible. None of it guarantees nothing will ever go wrong.
What it does is simple and powerful:
When something leaks somewhere, it doesn’t take your entire digital life with it.
That’s not advanced security.
That’s basic digital resilience.